Spotify’s Free Tier Redesigned: Improved Control, Personalization, and Exciting Updates
We independently review everything we recommend. When you buy through our links, we may earn a commission which is paid directly to our Australia-based writers, editors, and support staff. Thank you for your support!
Quick Overview
- Spotify upgrades its free tier with new features for enhanced control and customization.
- Users can now search, play, and share any song immediately without needing a Premium account.
- Customized playlist covers and daylist functions bring character and mood-driven music curation.
- Discover Weekly and Release Radar playlists are now accessible to free-tier users.
- Real-time lyrics feature boosts music interaction by enabling sharing on social networks.
- Updates are available in Australia at no additional cost.
Improved Control and Customization
Spotify has launched a worldwide update to its free tier, simplifying music discovery and enjoyment through improved control and customization choices. This update introduces various features that were once exclusive to Premium users, closing the divide between free and paid experiences.
Easy Search & Play
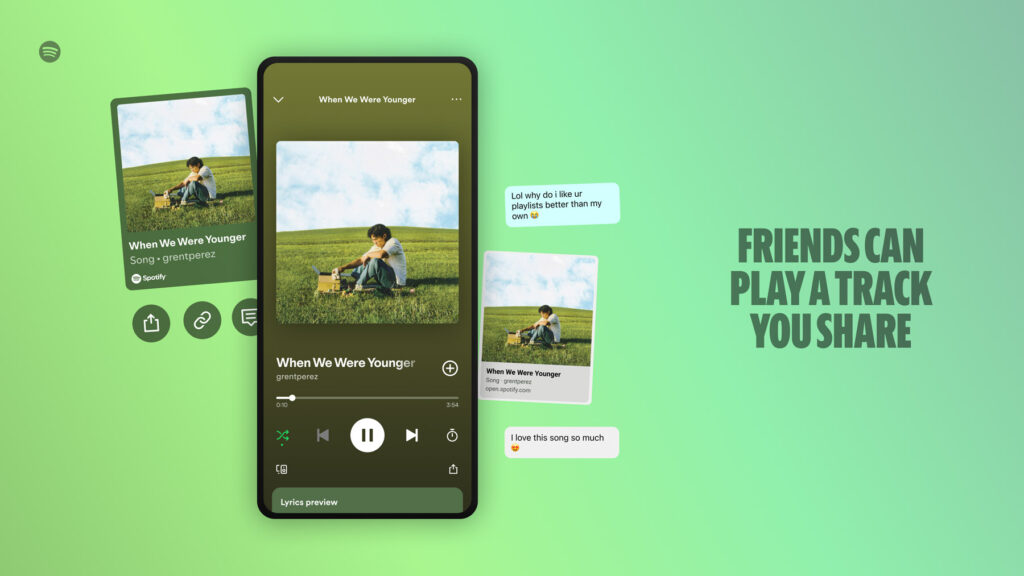
With the latest update, free-tier users can quickly search and play tracks instantly, creating a more fluid experience. Whether it’s a trending song or a friend’s suggestion, enjoy listening without limitations.
Share & Enjoy with Friends
Spotify now enables users to simply click and listen to tracks shared by friends or posted by artists on social media, keeping them connected with the newest releases and suggestions.
Playlists: A Personalized Musical Experience
Creating and Curating Playlists
Forming playlists is more straightforward than ever, with Spotify’s algorithm recommending songs that fit your mood. This assists users in effortlessly uncovering new artists and genres.
Personalized Playlist Covers
Users can now customize their playlists with unique cover art directly within the Spotify mobile app, making their music library more distinctive and personal.
Daylist Feature
The daylist feature creates playlists tailored to your listening patterns throughout the day, offering mood-specific music that can be stored for later enjoyment.
Exploring New Music
Discover Weekly and Release Radar
Spotify’s Discover Weekly and Release Radar playlists are now available for free users, offering tailored suggestions and the latest tracks from followed artists.
Real-Time Lyrics
The lyrics feature allows users to view real-time lyrics, augmenting the listening experience and enabling them to share their favorite lines on social media channels.
Importance for Australian Users
These updates are accessible without any changes to pricing, making Spotify’s free tier an appealing choice for music lovers in Australia. Users can enjoy enhanced features simply by updating their Spotify app.
Spotify continues to dedicate resources to making its platform a lively space for music fans and creators, ensuring a rich auditory experience for all users.
Conclusion
The new updates to Spotify’s free tier provide a more engaging and personalized experience for users in Australia. With features like immediate track play, custom playlists, and real-time lyrics, Spotify enhances music exploration and enjoyment without extra costs.